U.S. Army looks to Daphne Yao to provide a more secure cyberspace
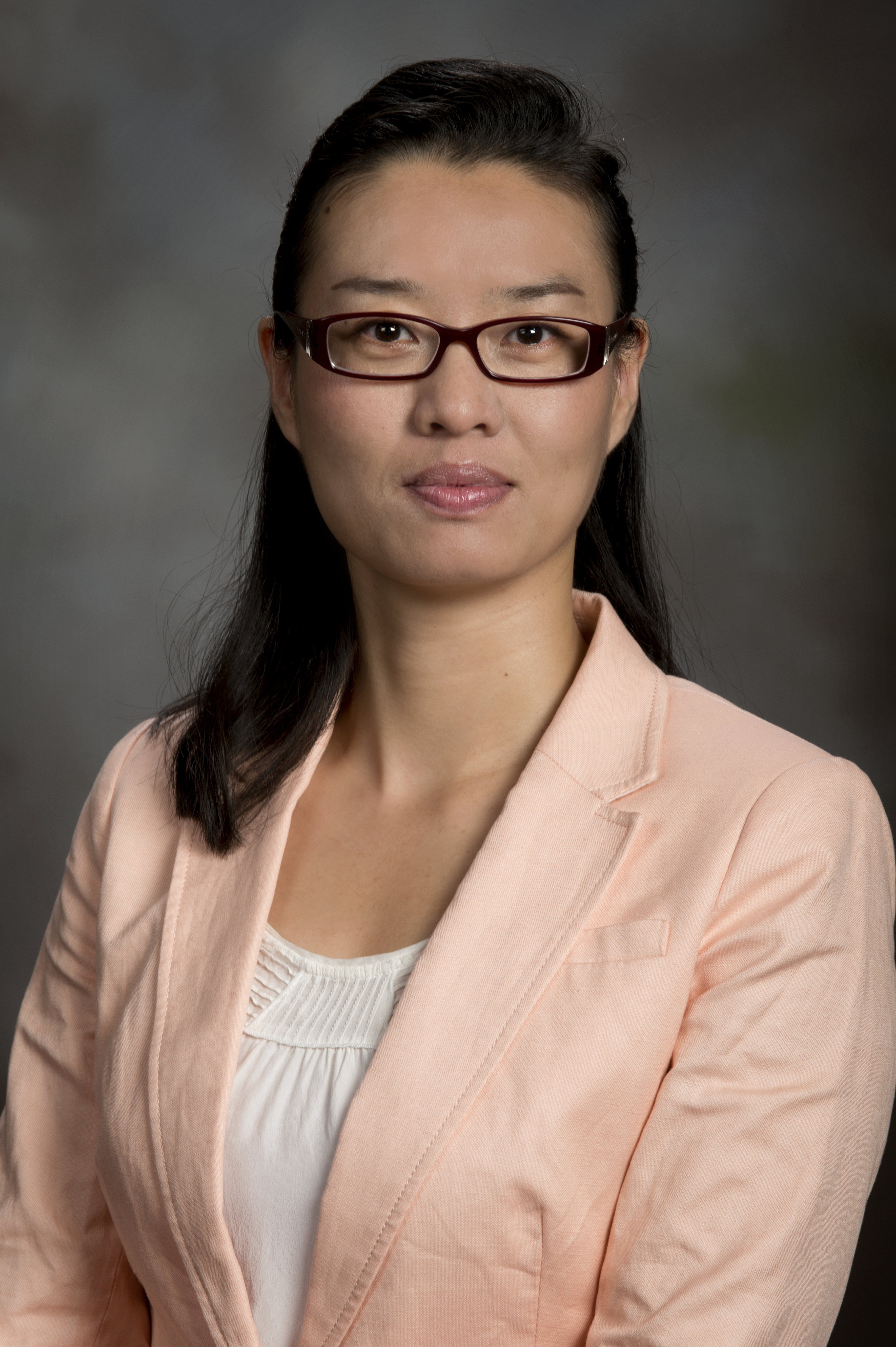
In cybersecurity, "the detection of insider attacks is a problem that we have known for a long time to be notorious to solve," said Daphne Yao, the newly appointed L-3 Fellow and associate professor of computer science at Virginia Tech.
The U.S. Army agrees with her. It just awarded Yao an Army Research Office Young Investigator Award "to detect anomalies that are caused by system compromises and malicious insiders."
The $150,000 award will allow her to design big data algorithms that will focus on discovering logical relations among human activities. This research ranges from the analysis of low-level machine events to the reasoning about the legitimacy of human activities with respect to organizational security goals. She will look for abnormal action sequences and workflows.
Recording this type of data "can be useful for detecting insider attacks," said Yao who previously won a National Science Foundation CAREER award to develop software that differentiated human-user computer interaction from that of malware, commonly known as malicious software.
Today's military operations must have trustworthy networked systems in both the cyberspace and the physical world, and the importance of real-time surveillance is critical.
"If we are successful, our proposed solutions will provide a leap forward to stronger Army command and control of cyberspace capabilities on the battlefield as well as in day-to-day operations," Yao said. Preliminary studies prior to the awarding of the young investigator award have shown promising results.
Yao seeks to provide trustworthy data and an infrastructure that will support a variety of military needs. They include a soldier's mobile computing device, people inside an armored fighting vehicle with a network embedded system, and operators using satellite links to connect a command station with those in the field.
"One key insight that inspires our approach of triggering a discovery is that human security experts tend to analyze the underlying relations of event occurrences as opposed to treating them independently," Yao said. "Triggering relations among cyberspace events at all levels can provide powerful evidence for system and network assurance status."
Otherwise, Yao believes, events that happen in the cyberspace network are not placed in context.
The type of system assurance Yao envisions is a guarantee that when a user enters a password, the computer is free of spyware key-loggers and/or that the organizational network is free of compromised computers that may be controlled by malicious outsiders.
The host of the operating system and software could include: a workstation, a laptop, a server, an embedded system, or a mobile smart phone. The network assurance would be between these multiple hosts.
"Because almost all modern computing devices are connected to networks, system assurance and network assurance need to be addressed together," Yao said.
Yao's 2010 NSF CAREER Award allowed her to effectively isolate infected computer hosts and detected in advance stealthy malware. Her work was highlighted at the 2014 ACM Symposium on Information, Computer, and Communications Security in Kyoto, Japan.
When she announced her findings in Japan, she said at that time that, "This type of semantic reasoning is new and very powerful. The true significance of this security approach is its potential proactive defense capability. Conventional security systems scan for known attack patterns, which is reactive. Our anomaly detection based on enforcing benign properties in network traffic is a clear departure from that."